Jellyfish Inspired Lodges To Help Clean The Environment – Secret Energy
Robot ‘jellyfish’ with ‘tentacles’ that catch trash and clean polluted water
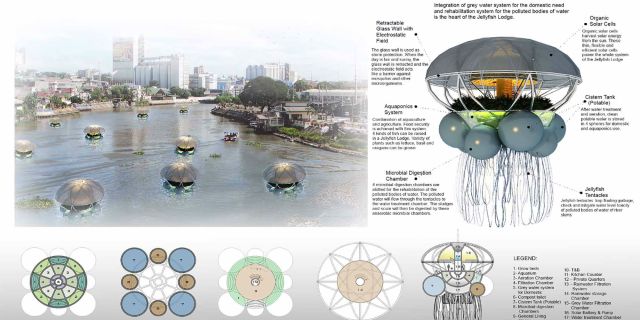
The Jellyfish Lodge is a concept conceived by architect Janine Hung for Inhabitat’s Biodesign Competition. They boast kitchen and bathroom-equipped living quarters and even vegetable gardens in their base. They have long ‘tentacles’ leading into the surrounding river which traps and collects rubbish and also filters polluted water.

When it comes to design, mother nature has a lot to teach us. The field of Biodesign has emerged as an exciting new discipline which integrates the best ideas from nature with the cutting edge of modern technology, fostering technological breakthroughs that could allow us to live better lives, more in harmony with our environment. The Jellyfish Lodge proposes to
Source: Jellyfish Inspired Lodges To Purify Environment | Secret Energy
Printable Medicine To End Animal Testing
A breakthrough in 3D, printable medicine has enabled engineers to create human ‘organs’ on a microchip, fully usable for testing against drugs and toxins. They are not actual organs, but, instead, a layer of six types of ink, all printed in a combination that causes the chip to react as if it were the actual organ. They have, specifically, recreated
Google Is Cutting the Cord on Its Fiber Rollout
Health Risk: 5G Ultra-High Frequency Radiation Is Coming
The 5G revolution is rushing toward us and it will bring a whole new era of harm from ultra-high microwave frequency radiation. And those who raise their voices against the danger to our health and our human rights to safety have been the subject of harassment, intimidation and attempts to silence them. ‘Stay out of the way of technological development.’
Source: Health Risk: 5G Ultra-High Frequency Radiation Is Coming
The internet is controlled by secret keys – Business Insider
A highly scripted ritualThe physical keys unlock safe deposit boxes. Inside those boxes are smart key cards. It takes multiple keys to gain access to the device that generates the internet’s master key.That master key is really some computer code known as a root key-signing key. It is a password of sorts that can access the master ICANN database. This key generates more keys that trickle down to protect various bits and pieces of the internet, in various places, used by different internet security organizations.The security surrounding the ceremonies before and after is intense. It involves participants passing through a series of locked doors using key codes and hand scanners until they enter a room so secure that no electronic communications can escape it. Inside the room, the crypto officers assemble along with other ICANN officials and typically some guests and observers.The whole event is heavily scripted, meticulously recorded, and audited. The exact steps of the ceremony are mapped out in advance and distributed to the participants so that if any deviation occurs the whole room will know.The group conducts the ceremony, as scripted, then each person files out of the room one by one. They’ve been known to go to a local restaurant and celebrate after that.But as secure as all of this is, the internet is an open piece of technology not owned by any single entity. The internet was invented in the US, but the US relinquished its decades of stewardship of DNS earlier this month. ICANN is officially in charge.Keenly aware of its international role and the worldwide trust placed on it, ICANN lets anyone monitor this ceremony, providing a live stream over the internet. It also publishes the scripts for each ceremony.On October 27, ICANN will hold another ceremony — and this one will be historic, too. For the first time, it will change out the master key itself. Technically speaking, it will change the “key pair” upon which all DNS security is built, known as the Root Zone Signing Key.”If you had this key and were able to, for example, generate your own version of the root zone, you would be in the position to redirect a tremendous amount of traffic,” Matt Larson, vice president of research at ICANN, recently told Motherboard’s Joseph Cox.Here’s an in-depth description of the ceremony by CloudFlare’s Olafur Guomundsson.Here’s a video of the very first key ceremony, conducted in 2010. Skip to 1:58 to see it.
Source: The internet is controlled by secret keys – Business Insider